The digital landscape is fraught with complexities, especially when it comes to privacy and security. As technology continues to evolve, so do the tools that threaten our safety. One such tool is Pegasus spyware, which has become notorious for its ability to infiltrate devices without the user’s knowledge. Recently, this topic gained further notoriety with an email dubbed "hello pervert," bringing to the forefront the unsettling implications of surveillance in our daily lives. This article aims to explore the depths of this incident, shedding light on the dangers posed by Pegasus spyware and the broader implications for privacy and security.
As the world becomes more interconnected, the potential for misuse of technology grows exponentially. The "hello pervert" email incident raises significant questions about who is watching us, how they gain access to our information, and what can be done to protect ourselves in a world where digital privacy is increasingly compromised. The rise of Pegasus spyware is a chilling reminder of the surveillance capabilities available to those with malicious intent.
In this article, we will delve into the specifics of the Pegasus spyware, the implications of the "hello pervert" email, and the broader context of digital privacy. With rising concerns about surveillance and hacking, it is crucial to understand the tools at play and how they can impact not only individuals but also society as a whole. Let’s embark on this exploration of Pegasus spyware and its troubling associations, including the infamous email that has caught the public’s attention.
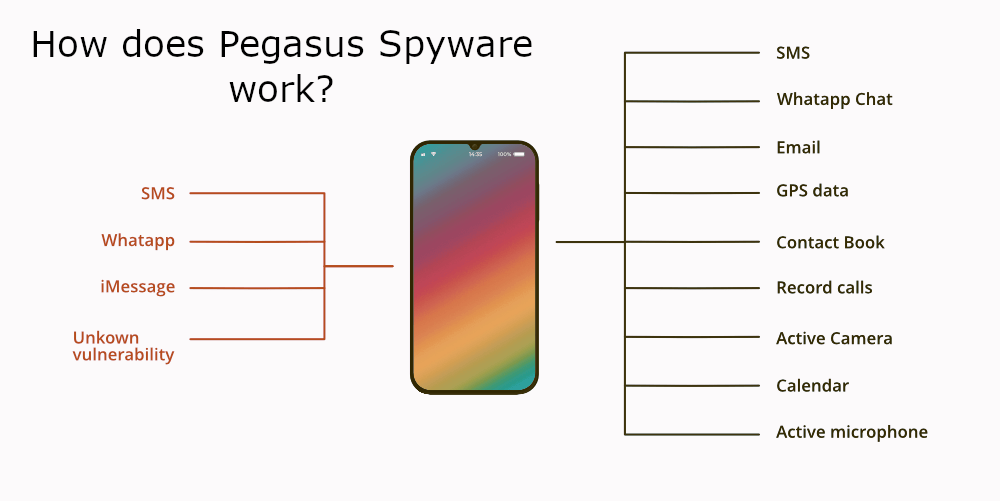
What is Pegasus Spyware and How Does It Work?
Pegasus spyware is a sophisticated piece of malware developed by the Israeli cyber intelligence firm NSO Group. It is designed to infiltrate mobile devices, allowing hackers to access sensitive data, track location, and even activate cameras and microphones without the user’s consent. The spyware can be installed through various methods, including malicious links sent via text messages or emails. Once installed, it operates stealthily, making it difficult for victims to detect its presence.
How Did the "Hello Pervert" Email Come to Light?
The "hello pervert" email incident surfaced when a group of journalists and activists discovered that their devices had been compromised by Pegasus spyware. The email, seemingly innocuous, was a trap designed to entice users into clicking a malicious link that would install the spyware on their devices. This incident highlighted the lengths to which attackers would go to exploit vulnerabilities in digital communication.
Why is the "Hello Pervert" Email Significant?
The "hello pervert" email is significant for several reasons. Firstly, it showcases the evolving tactics used by cybercriminals to deploy malware. Secondly, it raises awareness about the potential for ordinary emails to serve as vectors for cyberattacks. Lastly, it serves as a reminder of the importance of digital literacy and vigilance in an age where personal data is continuously under threat.
What Are the Implications of Pegasus Spyware for Personal Privacy?
The implications of Pegasus spyware on personal privacy are profound. Individuals who fall victim to this spyware may find their most intimate conversations, photos, and personal information exposed to malicious entities. This not only violates privacy but can also lead to severe emotional distress, reputational damage, and even physical danger in extreme cases.
How Can One Protect Themselves from Pegasus Spyware?
In light of the threats posed by Pegasus spyware, it's essential to take proactive measures to safeguard personal data. Here are several strategies to enhance your security:
- Regularly update your device software to patch security vulnerabilities.
- Be cautious of unsolicited emails and links, especially from unknown sources.
- Utilize strong passwords and enable two-factor authentication on sensitive accounts.
- Install reputable security software that can detect and block malware.
- Educate yourself about the latest cyber threats and tactics used by attackers.
Can Governments Regulate the Use of Spyware like Pegasus?
The regulation of spyware like Pegasus presents a complex challenge. On one hand, governments must protect their citizens from cyber threats; on the other hand, the use of such powerful surveillance tools raises ethical questions. Striking a balance between security and privacy is imperative, and discussions surrounding legislation and oversight are crucial in preventing abuse of power.
Is There a Way to Track the Spread of Pegasus Spyware?
Tracking the spread of Pegasus spyware involves monitoring data breaches, analyzing traffic patterns, and utilizing cybersecurity tools. Organizations and researchers work tirelessly to uncover instances of spyware infections and identify the tactics employed by attackers. However, due to the covert nature of this malware, tracking its spread can be a daunting task.
What Can Be Done to Raise Awareness About Pegasus Spyware?
Raising awareness about Pegasus spyware is essential in empowering individuals to protect themselves. Here are some effective strategies:
- Conduct workshops and seminars on digital privacy and security.
- Create informative content that highlights the dangers of spyware.
- Engage in discussions on social media platforms to spread awareness.
- Collaborate with cybersecurity organizations to amplify the message.
Is There Hope for a World Without Spyware?
While it may seem daunting, there is hope for a future where spyware is less prevalent. By advocating for stronger privacy laws, investing in cybersecurity infrastructure, and enhancing public awareness, society can work towards reducing the threat posed by surveillance tools like Pegasus. It will require collective effort, but a world that respects digital privacy is within reach.
In conclusion, the "hello pervert" email incident serves as a stark reminder of the ongoing battle for privacy in the digital age. As we continue to navigate this landscape, it is crucial to remain vigilant and informed about the tools that threaten our safety. By understanding the implications of Pegasus spyware and taking proactive measures, we can better protect ourselves from the pervasive reach of surveillance technology.